Useful System Tools Hidden in Windows part 7
How to Open the Local Group Policy Editor’s Guide in Windows XP, 7
Group Policies are one of the most useful, complex and overlooked tools available in Windows XP/7. Group Policies are rules that can be applied to a machine every time the operating system starts up. These rules can be used to significantly improve the baseline security of the operating system, on the global or local level. Although primarily intended for use in corporate environment, there is no reason why a home user should not benefit from them.
Group Policies allow you to control the registry, security options, scripts, folders, and software installation and maintenance. The last set of rules is called the Software Restriction Policies. In fact, Software Restriction Policies are a subset of the Group Policies.
Group Policies can be enforced per computer or per user. This means that you will be able to use certain accounts with full privileges while others will have limited options and usability. Software Restriction Policies can only be set globally. Do note that Group Policies cannot be set or edited when running under a limited user account.
What are these Policies actually good for?
Many Windows users invest time and money in buying security software that is intended to guard different parts of their operating system and protect from changes. Not surprisingly, many programs of this kind do things that can be accomplished with Group Policies. This means that you do not have to invest your resources in buying third-party software and finding the right balance of compatibility with your existing setup. The built-in tools will do.
The Policies will be particularly useful for the following setups:
Multi-user environment where the owner wishes to control other users
You can use the Policies to limit specific users from doing things you might not want them to do, like installing extra software or tweaking with different settings. This can be very useful when the target audience are people who have are computer-illiterate (older people, usually) or computer-obstinate (teenagers). For instance, you’re a university student and you share your PC with your flatmate, who is, for the lack of a better word, dumb. If you have no money and do no wish to hurt your friend, even though he insists on installing ActiveX controls every time he sees one, Group Policies could do the trick.
Single-user environment where the owner wishes to tighten the security
These days, you will often hear words like ‘zero-day exploits’ circulating in the security-savvy circles and you might feel a slight wave of paranoia overtaking you. Instead of piling tons of programs just to keep away the doomsday virus from your machine, you can deploy a few simple policies and prevent the disaster from ever getting conceived.
Group Policies are highly effective, do not toll the resources and require minimal maintenance, once fully configured. The only apparent catch is that you will need to learn how to use the Policies. For most people, this is a completely unknown territory, and they might feel slightly overwhelmed or even discouraged from exploring it.
Luckily, things are not as frightening as they seem. Besides, hopefully, this mine article will be able to help you take the first few steps. That said, I wish to emphasize that this article is by no means a full, comprehensive formula for making it right. There are virtually limitless possibilities when it comes to configuring the Group Policies, especially bearing in mind that they should be set to suit YOUR needs.
My surfing habits are most likely different from yours (unless you are my brother), which means that you should not blindly take my examples as the holy grail of security. Instead, you should use this guide to familiarize with Group Policies, learn how to use them and from there, develop your own strategies.
Before we start, a few useful tips:
- Do not apply more than a few settings at once! If something goes wrong, you might not be able to easily isolate the source of the problem.
- You should backup your data before trying for the first time.
- You should probably set a System Restore point.
- You need lots of patience.
- Optional but warmly recommended: If you can, install VMware Player or Server. Learning about Group Policies and Software Restriction Policies can be rather harmless if you do it in a virtual machine running a guest Windows XP,7 operating system.
How do you access the Group Policies?
If you are running Windows XP Pro under an administrator-type account, you can invoke the Group Policy Object Editor by typing gpedit.msc in the Start > Run field.
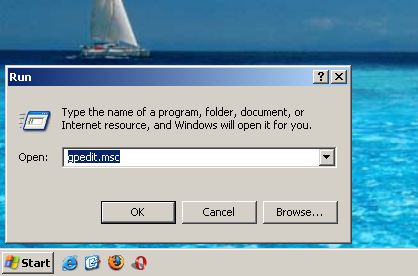
This command will open the Group Policies Object Editor. You can identify the running process as mmc.exe in the Task Manager. This process belongs to Microsoft Management Console; Group Policy Object Editor is a part of the MMC.
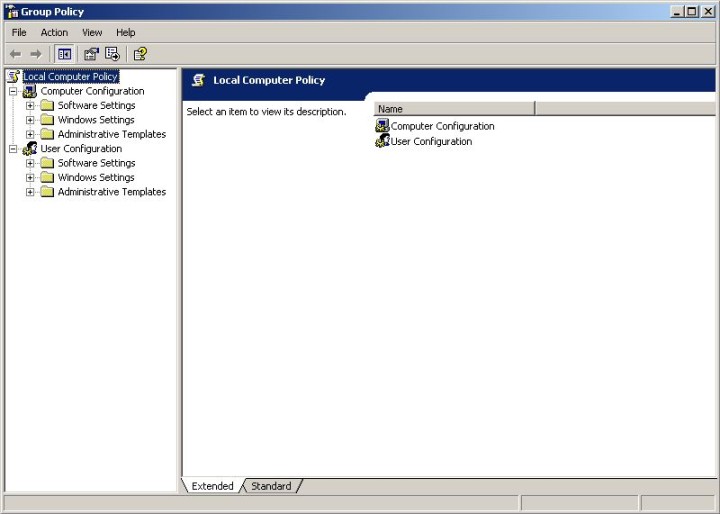
For the time being, nothing special is happening. On the left side, you have the tree of available settings, in the hierarchal (pyramidal) structure. This is the Console Tree. If you select an option on the left, it will be presented in detail in the right pane, including a brief if very useful description of its basic parameters. The right pane is called the Details Pane.
The Group Policies can be applied on global level (Computer Configuration) or user level (User Configuration). Most options are identical for the two. Certain options will be available only globally or locally.
What now?
It is very easy to get lost even before you start. You need to have a CLEAR idea what you wish to do. If you are just starting and wish to experiment, then go ahead. However, if you are setting your machine for a working environment, I suggest you carefully plan your goals. You might even consider using pen and paper to organize your setup.
First, who is the intended user?
You? Someone else? If so, what is his / her level of expertise? What are his / her habits? For example, spending an hour tweaking Internet Explorer settings might be a bad choice if the intended user NEVER bothers to open the Internet Explorer to browse. However, if the person is prone to download lots of software and run executables without check, you might wish to restrict his / her ability to start programs that are not explicitly allowed.
Second, what are you trying to achieve?
Do you wish to ruthlessly crush one’s ability to use the machine or merely wish to minimize the possibility of unintentional damage through inexpert use? You should adjust your setup to reflect the reality and help improve functionality and performance rather than change them completely. You will know you have succeeded in your task when the target audience continues using the machine without any apparent changes.
Third, slow down
Most importantly, do not overdo it. Having discovered a new toy, you will probably feel compelled to try everything at once. This will result in a severely crippled machine that you might end up formatting in sheer frustration of your own undoing. Now that we have established these basic rules, let’s begin.
Software Restriction Policies
Software Restriction Policies allow you to control the execution of programs on your computer. This subset of policies is by far the most important part of your policies management. If you set them up correctly, you will have saved yourself quite a lot of work with other policies. Software Restriction Policies are located under:
Local Computer Policy > Computer Configuration > Windows Settings > Security Settings > Software Restriction Policies
Software Restriction Policies have two basic levels: Disallowed – All executables will be prevented from running, save a list of approved programs (whitelist). Unrestricted – All executables will be allowed to run, save a list of forbidden programs (blacklist). The first level should be used when you wish to allow only certain applications to run. This method is a bit dangerous, as it requires that you fully understand which processes should be allowed to run and that you will be able to solve problems should you encounter one. It is also less flexible, as it will limit you to a fixed set of allowed executables.
The second level should be used when you wish to limit only certain applications from running. This method is easier to setup correctly, but it leaves a rather large degree of freedom to the intended user.
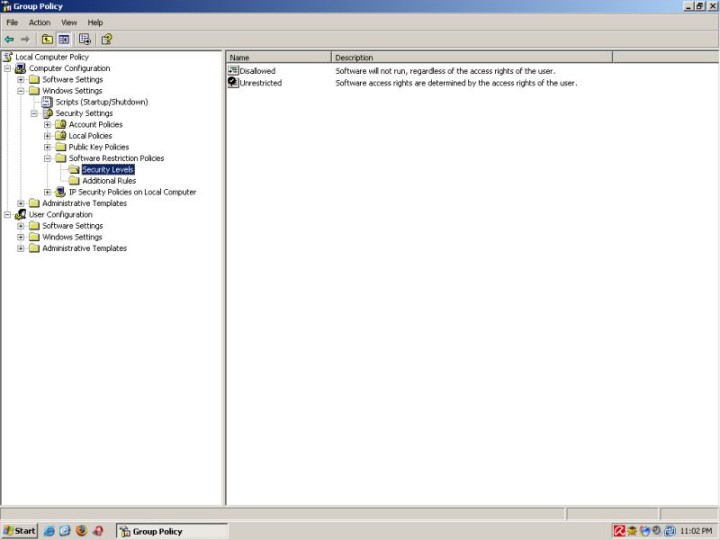
If you’re only starting, I suggest you try the default Unrestricted security level and build specific rules for the undesired applications. Once you master the use of Policies, you might want to try the Disallowed level.
Additional rules allow you to specify executables that you wish to exclude from the default level. In other words, specify the whitelist or the blacklist, depending on your choice.
To keep you from locking yourself out of the system, the core Windows processes are listed as Unrestricted. Nevertheless, you should be careful, because there might be additional programs, like your firewall or anti-virus, that are most likely located elsewhere and will require their own rules, should you opt for Disallowed level. Another very important process that you would want to keep unrestricted is the Microsoft Management Console (mmc.exe), without which you will not be able to edit the Group Policies!
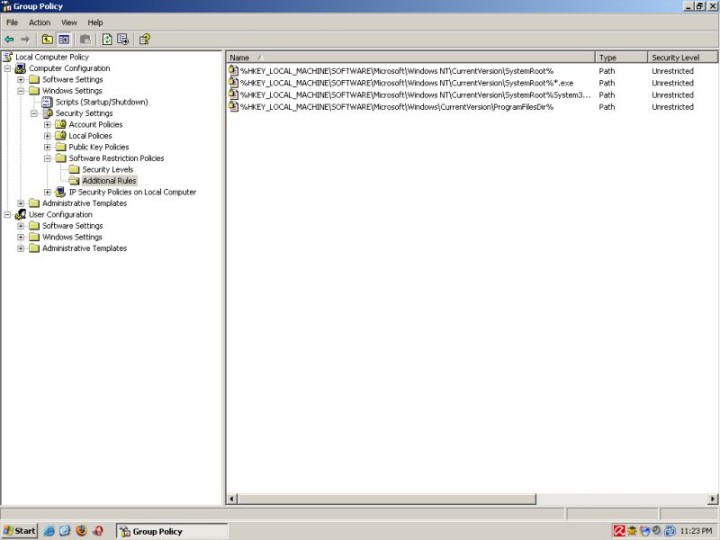
Adding a rule
There are several ways to create new rules:
- Highlight Additional Rules > right-click > choose a rule
- Highlight Additional Rules > right click in the Details Pane > choose a rule
- Highlight Additional Rules > Menu > Action > choose a rule
There are four types of rules – Hash, Certificate, Path, and Zone. These rules determine what files may or may not be run. For example, you can disallow a certain executable in one folder but allow it in another or block it completely using its hash value.
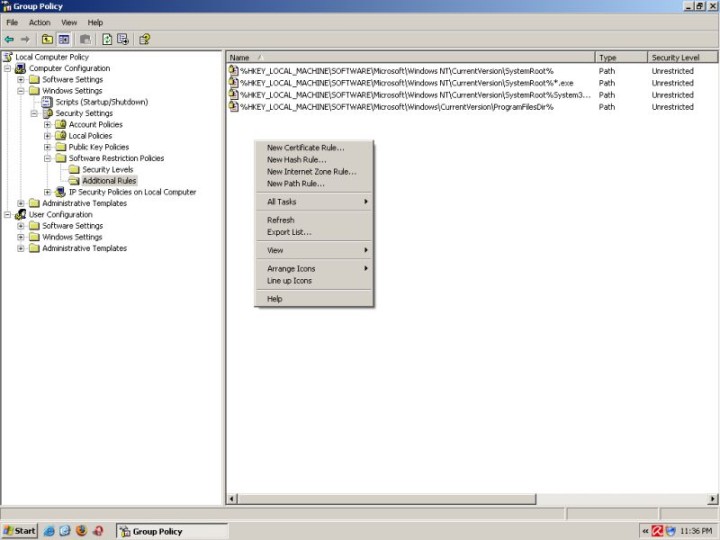
Example
I have create a file called virus.bat. It’s on the desktop. For all practical purposes, this file could be malicious. I will define a rule that will prevent it from running.
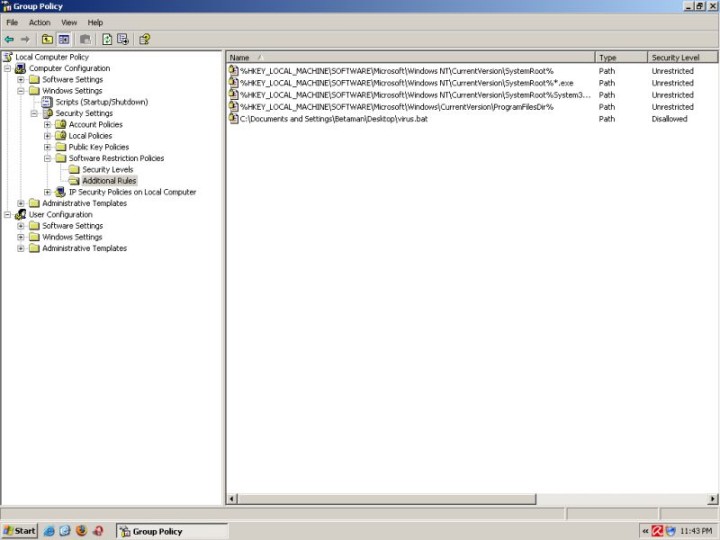
Indeed, when double-clicked on, the file will not run.
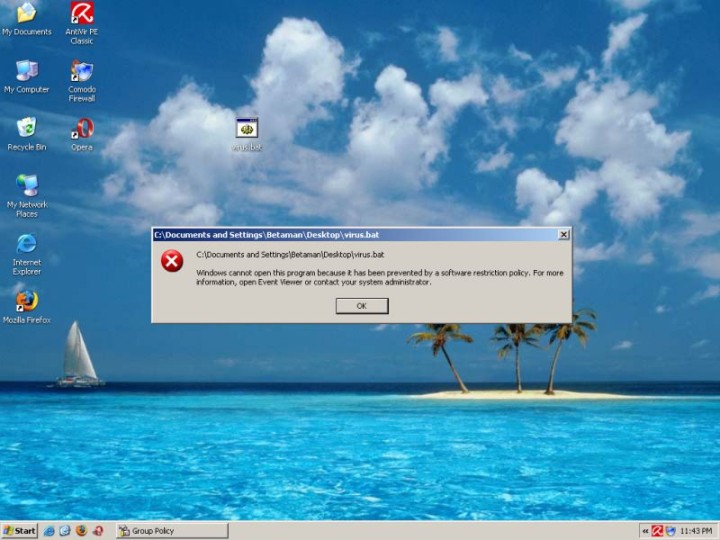
Technically, your imagination is the limit.
Other policies
Apart from software restrictions, you can also setup the working environment without explicitly relying on specific executables. A careless user can cause lots of damage even without running certain programs. Below is a very short and by no means an exhausting overview of some of the options that you can setup to control your machine and its human operators.
Internet Explorer
Setup Zones
You can use this options to configure each of the Zones in detail. For example, you can ban a user from downloading files in the Internet Zone, but allow it for sites listed in the Trusted Zone.
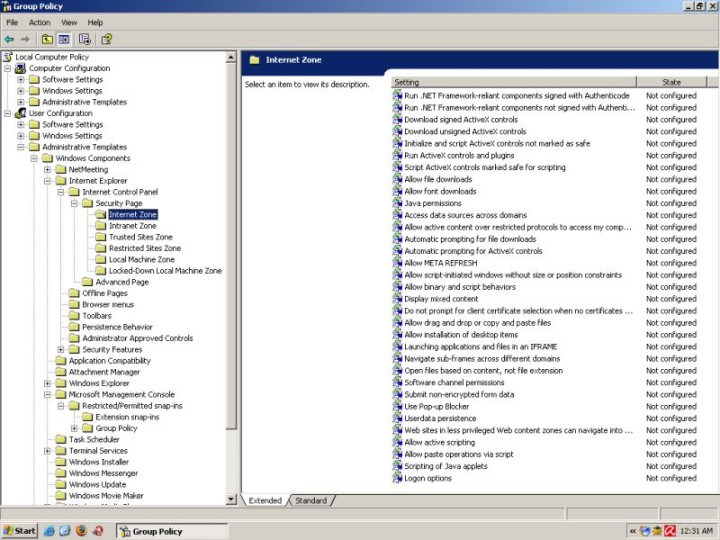
Disable active content on CDs
Remember the story with Sony DRM rootkit? Many people running Windows machines were infected with a rootkit simply by placing the music disc in the CD-ROM tray. What happened is that active content on the CD ran without user permission. Using this option would have been a good way of preventing it.
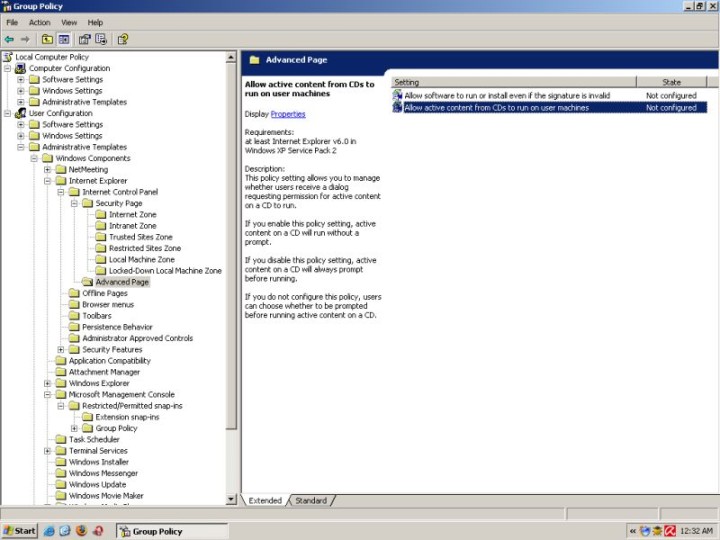
Restrict ActiveX control install
One of the nemeses of a typical Internet Explorer user are the ActiveX controls. You can keep them away completely.
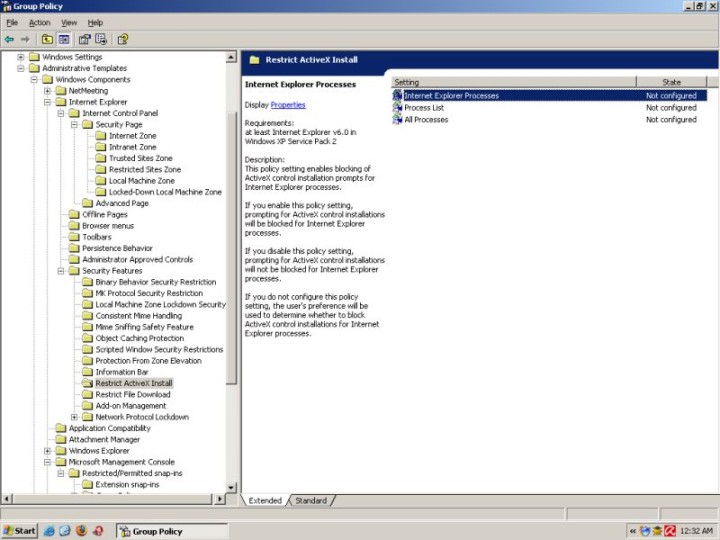
Windows Installer
Prevent removable media source install
One of the greatest dangers for any computer network is the presence of an insider, also known as Troy The Horse and Judah Iscariot. Many a wonderfully set-up network has been brought down by a careless user plugging in his USB flash disk and installing a program that he was otherwise unable to obtain from within the network.
Start Menu & Taskbar
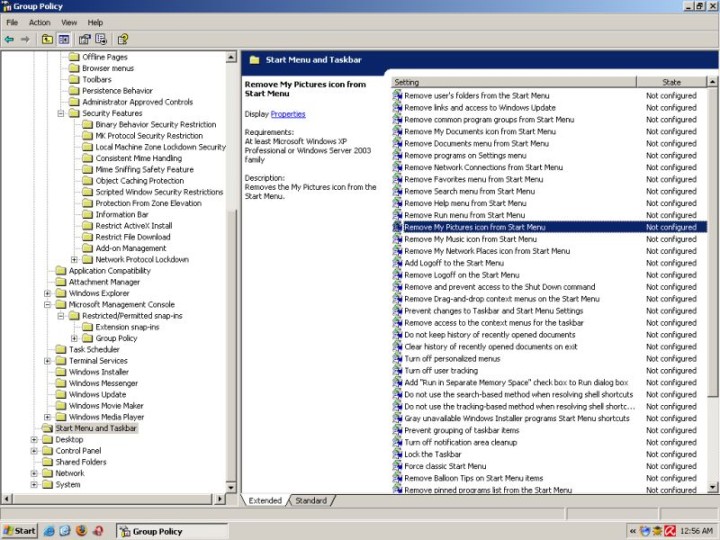
Remove My Pictures from Start Menu
You can also greatly customize the layout and functionality of your menus. For example, you can remove the extremely annoying My Pictures icon from the Start Menu. As well as tweak many other undesired functions and options.
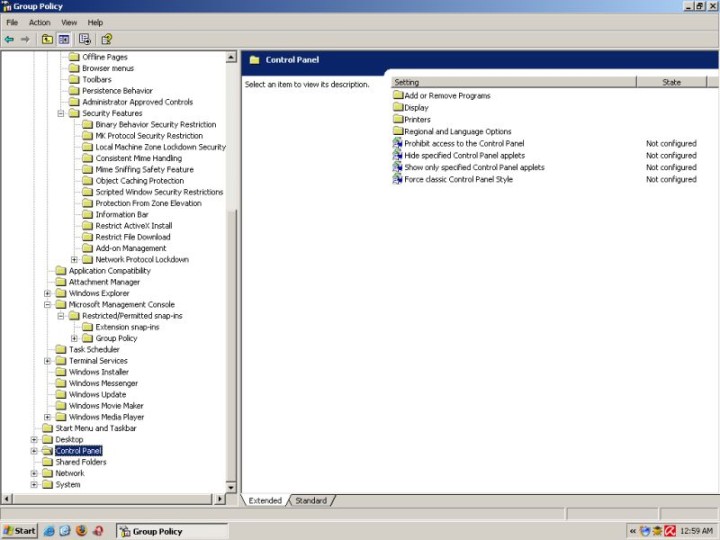
Control Panel
If you know that a certain user is going to be sorely tempted to tweak just about anything that he may find, you might want to restrict his access to the Control Panel or certain functions thereof.
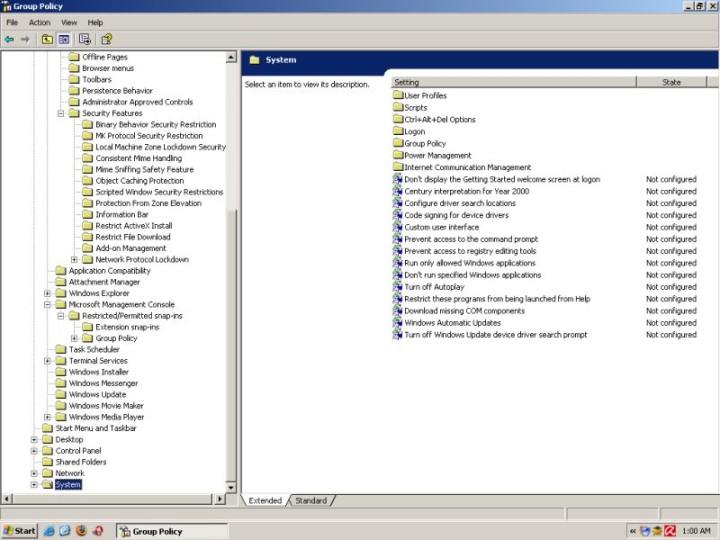
System
System-wise, you can prevent the user from accessing the registry, prevent access to the command prompt, run only some applications or bar him from running some others, disable autoplay of CDs, or configure Windows updates.
Some other, more useful policies that I can think of at the moment:
Computer Configuration > Windows Settings > Security Settings > Account Policies
Password Policy > Minimum password length
Password Policy > Password must meet complexity requirements
Account Lockout Policy > Account lockout threshold
User Configuration > Administrative Templates > Windows Components
Internet Explorer > Disable external branding of Internet Explorer
Internet Explorer > Pop-up allow list
Internet Explorer > Do not allow users to enable or disable add-ons
Internet Explorer > Internet Control Panel > Disable the … page (any or all)
Internet Explorer > Administrator Approved Controls > Configure to your liking
Windows Explorer > Hide these specific drives in My Computer
Windows Messenger > Do not allow Windows Messenger to be run
Windows Media Player > Playback > Prevent Codec Download
Start Menu and Taskbar > Do not keep history of recently opened documents
Start Menu and Taskbar > Turn off user tracking
Control Panel > Add or Remove Programs > Remove Add or Remove Programs
Control Panel > Display > Prevent changing wallpaper
Shared Folders > Allow DFS roots to be published (set to Disabled)
Network > Network Connections > Prohibit TCP/IP advanced configuration
Network > Network Connections > Prohibit access to properties of a LAN connection
Network > Network Connections > Prohibit access to the New Connection Wizard
The above sampling is just the tip of the iceberg. Going through all of them is impossible, because it means basically configure the entire Windows operating system, which is something that requires lots of time, careful planning and a personal touch. You should carefully browse through the available settings and decide what is the best choice for you.
Prevent other users from changing your settings
It is entirely possible that the user bearing the brunt of your choices is computer-savvy and has heard of Group Policies. In that case, he will be able to access the Group Policies snap-in and remove the offending rules. In that case, you need to prevent him from doing it. This his how you do it:
Disable the Microsoft Management Console (mmc.exe)
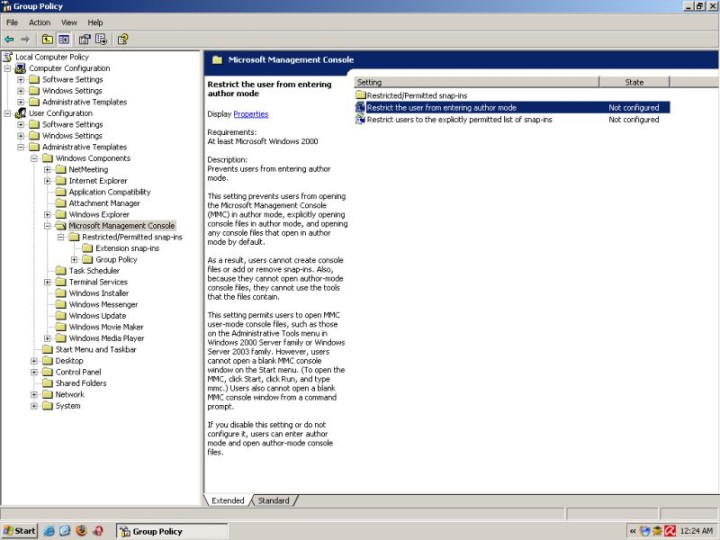
Disable Group Policy Object Editor (gpedit.msc)
Remember: Once you disable access to the Group Policy Editor, you will not be able to access it anymore except in the Safe Mode using the original Administrator account. This means that if you password-protect your Administrator account, you will be able to prevent other users from changing your settings.
And that’s it! You’re set. Your computer is now protected. Your policies are protected. Leak back and enjoy the silence.
Thanks, If you like this tutorial plz share this article to your friends in FB, Twitter,
In my next tutorial i will write about another hidden tool in windows Registry Editor