MEDIA ACCESS CONTROL – MAC ADDRESSES
What is a MAC Address?
Whether you work in a wired network office or a wireless one, one thing is common for both environments: It takes both network software and hardware (cables, routers, etc.) to transfer data from your computer to another or from a computer thousands of miles away to yours.
And in the end, to get the data you want right to YOU, it comes down to addresses.
So not surprisingly, along with an IP address (which is networks software), there’s also a hardware address. Typically it is tied to a key connection device in your computer called the network interface card, or NIC. The NIC is essentially a computer circuit card that makes it possible for your computer to connect to a network.
An NIC turns data into an electrical signal that can be transmitted over the network.
MAC addresses are physical addresses, unlike IP addresses which are logical addresses. Logical addresses require you to load special drivers and protocols in order to be able to configure your network card/computer with an IP Address, where as a MAC address doesn’t require any drivers whatsoever. The reason for this is that the MAC address is actually “the burned-in address (BIA)” into your network card’s memory chipset.
THE REASON FOR MAC
Each computer on a network needs to be identified in some way. If you’re thinking of IP addresses, then you’re correct to some extent, because an IP address does identify one unique machine on a network, but that is not enough.
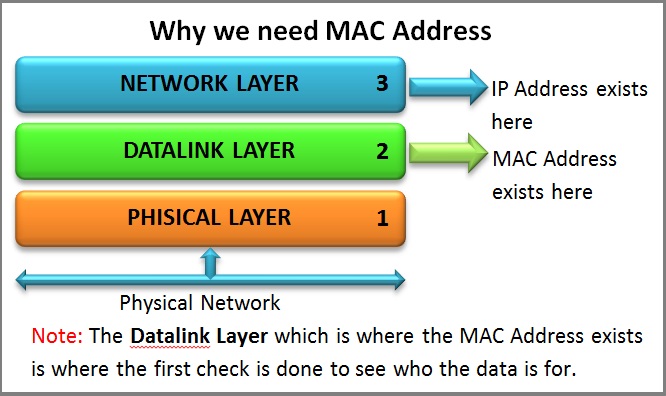
The diagram below provides a visual representation how important MAC Addresses are on our network and at which layer of the OSI Model they exist:
You see, the IP address of a machine exists on the 3rd Layer of the OSI model and, when a packet reaches the computer, it will travel from Layer 1 upwards, so we need to be able to identify the computer before Layer 3.
This is where the MAC address – Layer 2 comes into the picture. All machines on a network will listen for packets that have their MAC address in the destination field of the packet (they also listen for broadcasts and other stuff, but that’s analysed in other sections). The Physical Layer understands the electrical signals on the network and creates the frame which gets passed to the Datalink layer. If the packet is destined for the computer then the MAC address in the destination field of the packet will match, so it will accept it and pass it onto the Layer above (3) which, in turn, will check the network address of the packet (IP Address), to make sure it matches with the network address to which the computer has been configured.
EXAMINING A MAC ADDRESS
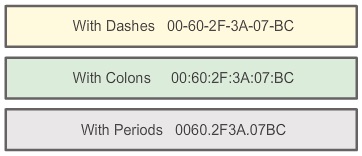
Let’s now have a look at a MAC address and see what it looks like! or how can we write MAC address!
Above figure we can see MAC address can write in three different ways With Dashes, With Colons, With Periods
As you’ve probably noticed, the MAC address itself doesn’t look anything like an IP address (see yours here). The MAC address is a string of usually six sets of two-digits or characters, separated by colons.
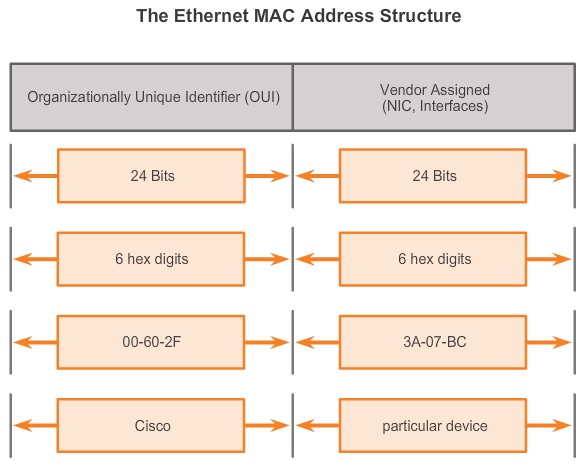
Some well-known manufacturers of network adapters or NICs are Dell, Belkin, Nortel and Cisco. These manufacturers all place a special number sequence (called the Organizationally Unique Identifier or OUI) in the MAC address that identifies them as the manufacturer. The OUI is typically right at the front of the address.For example, consider a network adapter with the MAC address “00-14-22-01-23-45.” The OUI for the manufacture of this router is the first three octets—”00-14-22.” let’s have a look of Ethernet Structure Of MAC Address in below figure;
Here are the OUI for other some well-known manufacturers.
Dell: 00-14-22
Nortel: 00-04-DC
Cisco: 00-40-96
Belkin: 00-30-BD
It’s common for the larger manufacturers of networking equipment to have more than one set of OUIs. visit this link ypu can get all the IEE standers developers and Vendor codes http://standards.ieee.org/develop/regauth/oui/oui.txt
Networks and MAC addresses.
All devices on the same network subnet have different MAC addresses. MAC addresses are very useful in diagnosing network issues, such as problems with IP addresses.
MAC addresses are useful for network diagnosis because they never change, as opposed to a dynamic IP address, which can change from time to time. For a network administrator, that makes a MAC address a more reliable way to identify senders and receivers of data on the network.
Wireless Routers and MAC Filtering
On wireless networks, a process called MAC filtering is a security measure to prevent unwanted network access by hackers and intruders. In MAC address filtering, the router is configured to accept traffic only from specific MAC addresses. This way, computers whose MAC addresses are approved will be able to communicate through the network—even if they were given a new IP address by DHCP.
Meanwhile, a hacker who’s hijacked a network IP address will be blocked because their MAC address will not be on the approved list and will be filtered out.
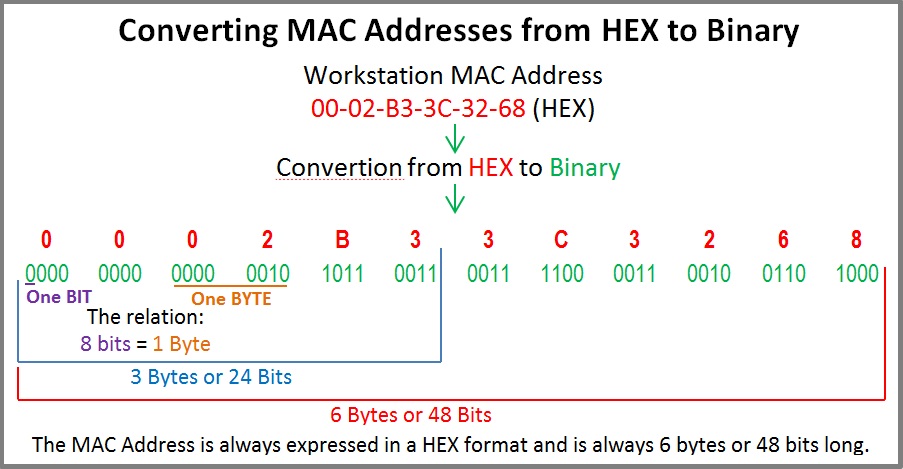
LET’S START TALKING BITS AND BYTES!
Now that we know what a MAC address looks like, we need to start analysing it. A MAC address of any network card is always the same length, that is, 6 Bytes long or 48 Bits long. If you’re scratching your head wondering where these figures came from, then just have a look at the picture below which makes it a bit easier to understand:
So that completes the discussion regarding MAC Addresses! I hope you have understood it all because it’s very important so you can expand your knowledge and truly understand what happens in a network !
Thanks, If you like this tutorial please share this article to your friends in FB, Twitter,